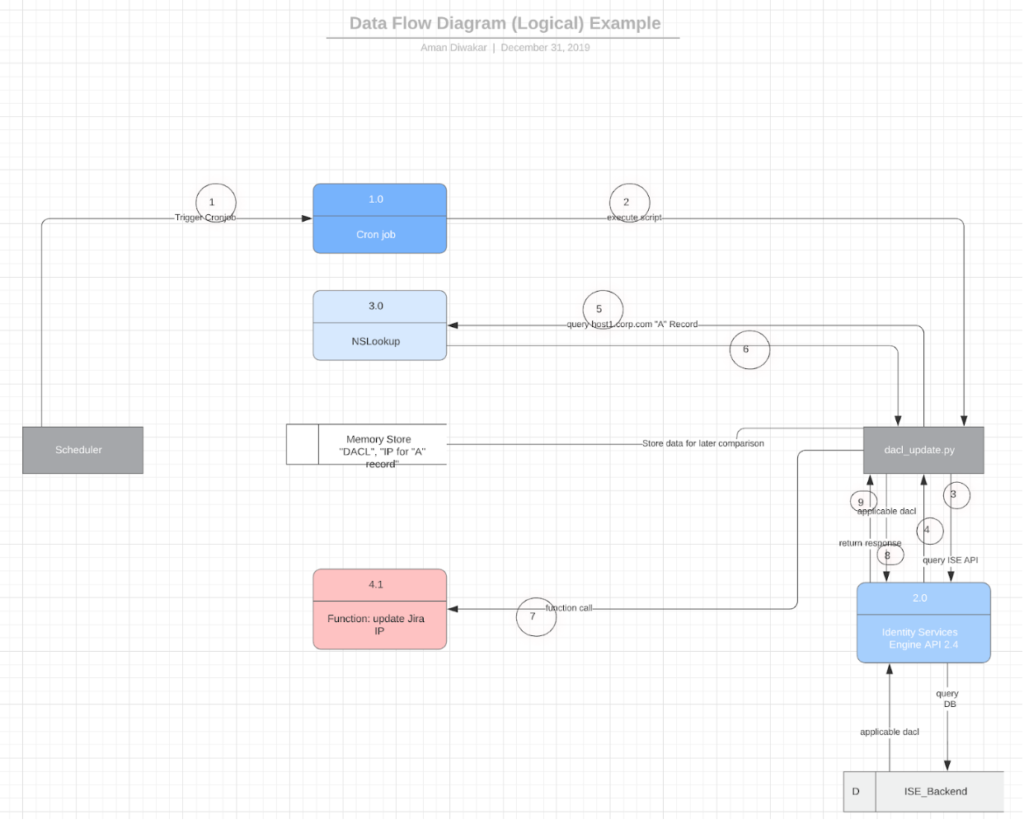
In this blog, we walk through the implementation of a Python script that checks if the IP for a DNS A record has changed, then automatically updates the ISE DACL.
Understand the ISE API
As with any other automation, understanding the flow and data source requirements is useful. In the attached diagram, I document the dataflow as well as important aspects of the scripts before writing it. Reading through Cisco’s ISE ERS API documentation is extremely useful here. The documentation includes enough information to get started, however, involves some trial and error. The “Update” PUT method allows you to update the DACL, and to my pleasure, it completely replaces the old DACL with a new one instead of simply appending lines to it. This makes life easier, as it simplifies regex substitution and insertion operations. Now that we understand the specific call we need to make, lets review other aspects of the API call. Some request fields are ISE version specific, such as the “ERS-Media-Type” header field. This field isn’t mandatory, however, it varies with ISE versions.
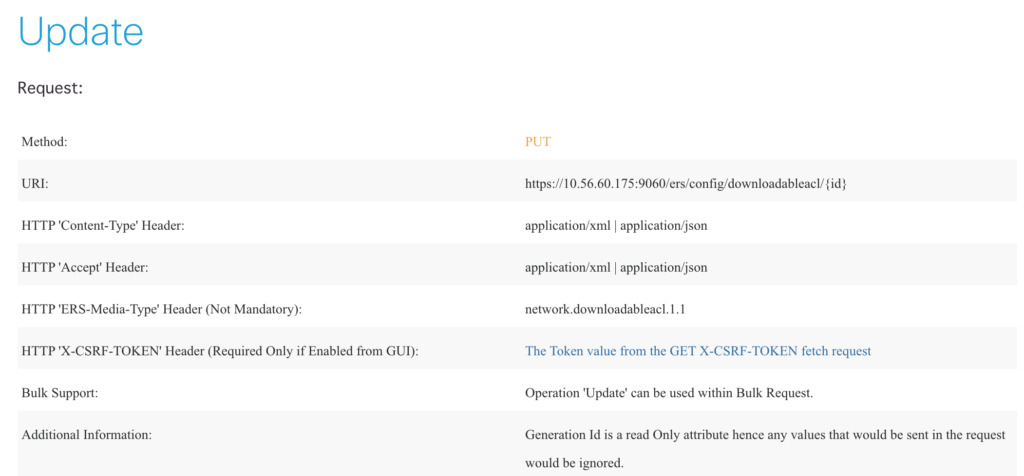
In order to get the DACL ID, you’ll first need to make a “Get-All” GET request. This will return all ACL IDs as well as their names in order to make identification easier. The PUT request is just a tad tricky and I’ll show you how to send the DACL in that request.
Get the right libraries
To make life easier, you’ll need a couple of libraries. Python’s “re”, “requests”, “json”, and “dns.resolver” libraries are needed in order to create requests, parse the JSON and finally, search through the dacl using “re”. The “dns.resolver” library parses the IP address of the A record easily.
First Expressions Count
One of the more challenging aspects of updating a string such as the DACL is finding the item to replace. I use remarks in the DACL to divide the larger piece into groups of IPs based on the application or server. I use “start” and “end” in the remarks to accomplish this. For example, “remark start app1.site.com” and “remark end app1.site.com” to identify a set of IPs associated with app1.site.com. I use regex101.com for helping parse and create expressions. The site can create expressions for a specific language which is extremely useful. An example of an expression is r”(?<=remark start app1\.site\.com\n)([\s\S]+?)(?=remark\send\sapp1\.site\.com)”.
Wrapping it up
The great thing about dns.resolver is that it provides a class-based approach to retrieving the IP portion of an “A” record. This saves us from using regex to search for the IP. To start with, we search and isolate the group of IPs associated with the application. Then, we find and replace those IPs with the ones returned by dns.resolver. Finally, we use the UPDATE API to PUT the newly updated DACL into ISE. The DACL goes in the payload and not the header section of the HTTP PUT, in another article, we’ll look at how we can use Postman to make our lives easier when testing out ISE APIs.